The Internet is rather popular. You probably use it quite a lot. If you do, it is worth spending a few minutes reading up on what a Virtual Private Network is, how it improves your privacy and how it provides access to hitherto unavailable services. I promise to keep the jargon to a minimum.
Nomads have particular reasons for getting themselves a VPN as it makes even their Internet traffic location-independent and keeps them safe in the multitude of internet cafes we call ‘office’.
What is a VPN?
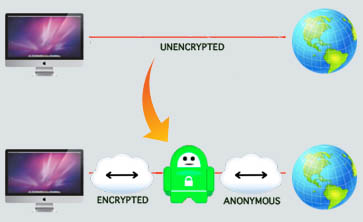
A VPN is one (or more) computers somewhere in the world through which you route your Internet traffic. By doing this, you solve two major privacy issues with the way the Internet works. This data redirection is done by a small program that you install on your computer. You can either set the program to always do this in the background, in which case you will never have to worry about it again, or you can choose to connect and disconnect from the VPN at will.
The owner of the VPN computer through which you route your data, called a VPN provider, doesn’t provide this service as a charity. They will charge for it, but it is usually a pretty low fee and very much worth it. Let’s find out why.
Privacy issue #1: Encryption
When you surf the web, you are sending and receiving lots of little bits of information called packages. But, let’s call them postcards as it is easier to visualize and reflects how easy they are to intercept and read.
Each postcard has three pieces of information on them:
- The content (e.g. Search: How do I treat crabs?)
- The recipient address (e.g. google.com)
- The sender address (e.g. IP 123.42.69.666)
Assuming you send the above ‘postcard’ while sitting at the local Starbucks, this is how it is going to be delivered.
- The postcard is broadcast openly to everybody at Starbucks.
- Starbucks’s Internet Service Provider (ISP, the company providing internet access to Starbucks) looks at the recipient address and forwards it to ‘the Internet’.
- Through some technical magic I’m not going to cover here, the postcard is handed from one computer to another until it finally reaches the recipient.
Having sent the above postcard, the shifty-looking person in the corner of Starbucks now knows you have crabs. It is really easy to intercept unencrypted data on a Wi-Fi network. And, the ISP also knows about your … situation. You might as well have stood up, clapped for attention and announced it.
Some websites have encryption to prevent people and companies snooping on the data you send and receive from them. (Encrypted sites have URLs that start with ‘https’.) Encrypted sites ensure that people can’t snoop on the content of your sent postcards.
However, the content of the postcard isn’t the only thing you should worry about. The recipient is also sensitive information, and it cannnot be encrypted!
For example, imagine you send this encrypted postcard:
- I lolovove yoyou! (Encrypted)
- To: justinbieber.com
- From: Comp. #5, Starbucks, London, UK
The content is encrypted, but the receiver is not. How could it be? If you encrypt it, then Starbucks’s Internet Service Provider wouldn’t know to whom it should send the postcard and neither would the many computers between Stabucks and Bieber HQ. It would be the same as writing “Someone, Somewhere” on an envelope and give it to your mailman.
So, the recipient is public information. Having sent the above postcard, both the Starbucks ISP and the shifty guy in the corner now knows that you are communicating with the Justin Bieber’s website. As any self-respecting company, the ISP will refuse to forward the postcard and tell you to grow up and start listening to real music. Many ISPs already do this with downloading sites such as Pirate Bay.
Illegal downloading is not the only case where this may be a problem. Let’s take another, more common, example. You spend a few hours on Facebook at work. Facebook is encrypted, so your boss won’t be able to see the dodgy weekend photos you posted, but she will know that you are messing about with social media during working hours, and for how long.
How a VPN improves Encryption.
A VPN sits between the ISP and the rest of the internet. You communicate with the VPN via encrypted messages, and the VPN then decrypt the messages and send them on to the final recipient. So, if you intend to send the following message …
- Do you treat Gonorrhoea?
- To: SexualDeceases-R-US.com
- From: Comp. #5, Starbucks, London, UK
… then your computer will actually send the follow postcard.
- Dodo yoyou totroreatot GoGononororrorhoea?
- To: Your VPN
- From: Comp. #5, Starbucks, London, UK
Mr Shifty and Starbucks’s ISP now has no way of knowing what your are sending/receiving or with whom you are communicating. All they can see is that you sent something to someone via your VPN.
Your VPN receives your postcard, decrypts it and sends a new postcard like this:
- Do you treat Gonorrhoea?
- To: SexualDeceases-R-US.com
- From: Your VPN
Someone might intercept this message and read it. It is, once it leaves the VPN, not encrypted anymore. But, this is much less likely as it is harder to wire-tap a transatlantic cable than it is to snoop on a coffee shop Wi-Fi network. But even if they do, the sender is now the VPN, not you.
The return journey is just the reverse. SexualDeceases-R-US.com replies with an open postcard to your VPN, the VPN encrypts the message and sends it on to you.
So, to recap, a VPN prevents hackers (on your local Wi-Fi network) and your Internet Service Provider from seeing what information you are sending/receiving AND with whom you are communicating.
Privacy issue #2: Identity and Location Transparency
So far we have been speaking mostly about you as the sender of information. But most of the time, you are requesting information. When you navigated to this post, you send me a postcard that looked a bit like this:
- Please send me your blog post on VPNs.
- To: themodernnomad.com
- From: Your IP address
I then sent you back this page via a postcard that looked a bit like this:
- Sure thing! Here it is. “The Internet is rather popular. You probably use it quite a …”
- To: Your IP address
- From: themodernnomad.com
But for this postcard to reach you, I had to know where to send it. That information is your IP address, and it can be used to figure out e.g. which country you are in. Don’t believe me? Well, does this look familiar to you?
I thought so. For surfing normal websites, this might not be so bad, but sometimes it is. Here are three random examples:
- You want to see the latest episode of Sherlock on the BBC iPlayer, but BBC sees that you are not in the UK and refuses, assuming no BBC License Fee payer goes abroad.
- You want to book a flight from Sao Paulo to Belo Horizonte, but the airline (TAM) sees that you are in the United States, assumes you are a rich guy and quotes you twice the normal Brazilian rate.
- You download an episode of True Blood via BitTorrent. HBO intercepts this traffic, sees that the recipient of this download was routed via your ISP, requests and receives your physical home address from the ISP and sends you threatening letters about legal action.
Obviously, these are all theoretical examples, and I don’t condone tricking the Commonwealth out of their license fee nor pirating… (I do however totally condone tricking TAM out of their selective pricing, the bastards…)
How a VPN gives you anonymity and location-independence.
The VPN computer through which you route your postcards is located somewhere in the world, and it has an IP address of that country. Most VPNs have servers all over the world, and you can choose to connect to any of them. All the people and services that you then communicate with will think that you are located where the VPN server is located.
Let’s take the BBC iPlayer example above and see how a VPN gets you access to UK-only services like the BBC iPlayer. First, you send a message like this:
- Give me the latest episode of Sherlock.
- To: BBC iPlayer
- From: Your IP address (incl. your country)
But your computer doesn’t actually send that message. Instead, it sends this message:
- Gogivove mome tothe lolatotesostot epopisosodode ofof Sosherorlolockok.
- To: Your VPN (in the UK)
- From: Your IP address (incl. your country)
The VPN gets the message, decrypts it and sends it on like this:
- Give me the latest episode of Sherlock.
- To: BBC iPlayer
- From: Your VPN (in the UK)
The BBC iPlayer says “sure, you are in the UK. Here is the Sherlock episode. Enjoy!” The VPN then sends it on to you, encrypted.
When you book your Brazilian flight via TAM a.k.a. “We rip off foreigners Incorporated,” you switch to a Brazilian VPN server. Want to listen to US-only Pandora? Switch to a US-based VPN server and off you go!
What about the third example, where some company goes to court demanding to know your identity? Well, they know that the information was send to the VPN, so they can ask the VPN to give out your identity. But, most VPNs do not record this information. As soon as they’ve routed the postcard on to you, they then shred the information about where they sent it. No matter how much legal pressure the VPN is put under, they can’t disclose something they don’t know.
How to select a VPN
I hope I’ve convinced you that a VPN is a useful service worth paying some money for. But how do you select a VPN? The main things to look for are as follows:

- They should not log or collect any information about their VPN routing.
- In which countries do they have servers?
- Do you like their VPN software? (the one that does the re-routing of your internet traffic)
- The cost.
- Can you connect multiple computers at once to them?
- Do they have any limits on the bandwidth?
- Do they have other useful features?
I did a fair bit of research and eventually I went with Private Internet Access. (Yes, that is the company name.) Here is how they stack up on the above metrics.
- Logs: They do not keep any logs of any kind. And, they are very clear about what information about you that they do store. To make it clear, they store some information about you as a customer, but nothing about your data traffic. They even invite you to use anonymous e-mail address for signup and to pay them using untraceable BitCoins!
- Server locations: US, UK, Canada, Switzerland, Sweden, Netherlands, France, Germany, Romania, HK.
- Software: I like their software. You can set it to connect automatically or manually, it is unobtrusive, easy to install and there is a version for Android phones as well.
- Price: $40/year or $7/month.
- Simultaneous devices: 5 at a time.
- Limits: No bandwidth limits.
- Extra Features: DNS/IP Leakage Protection, VPN Kill Switch, Port Forwarding.
I’ve used PIA many years now and I’ve been very happy with them. Two weeks ago, another VPN provider, Golden Frog VyprVPN, inquired if I wanted to review their product. I have now tried them a bit. In short, VyprVPN is similar to PIA with the following exceptions.
- Logs: They keep 30 days of logs. This would mean that they could give out your real IP address if requested by a court order.
- Speed: I tested the internet speed behind both VyprVPN and PIA. VyprVPN was faster, sometimes by a little and sometimes by a lot.
I’ll let you decide which is more important to you. If you have other recommendations, please leave them in the comments!
If you decide to get a VPN through the Private Internet Access company, then please sign up using this link. If you decide on VyprVPN, then please sign up using this link. Both links will generate a small commission for me. Thanks!




Most useful and accessible article on internet privacy I have ever read. You are an expert communicator, thank you.
Thank you! And if I know you at all, I imagine you might have read a few in the past. 🙂
One thing I didn’t get into (because it isn’t really connected with VPN directly) is that I’ve been hearing more and more about that anonymized data that companies hold can often be cross-referenced with other data sets to give a fair good guess at who is who.